Which of These Are Not Risk Factors for Potential Attackers? The Cybersecurity Guide Cybersecurity regulations and risk assessment requirements
If you are looking for Cybersecurity Risk Assessment Steps | The Untapped Potential you've visit to the right place. We have 25 Pics about Cybersecurity Risk Assessment Steps | The Untapped Potential like Cybersecurity Risk Assessment | FTG Australia, Risk Advisory | Cybersecurity Risks and also Best Practices To Prevent Cyber Attacks Cyber Risk Assessment PPT Template. Here you go:
Cybersecurity Risk Assessment Steps | The Untapped Potential
 uetechnology.net
uetechnology.net
Cybersecurity Regulations And Risk Assessment Requirements
 www.sans.org
www.sans.org
The No-Nonsense 6-Step Cybersecurity Risk Assessment Checklist — Etactics
 etactics.com
etactics.com
6 Reasons Why You Must Quantify Cyber Risk And IT Risk - Scrut Automation
 www.scrut.io
www.scrut.io
18 Best Practices For Risk Management In Cyber Security
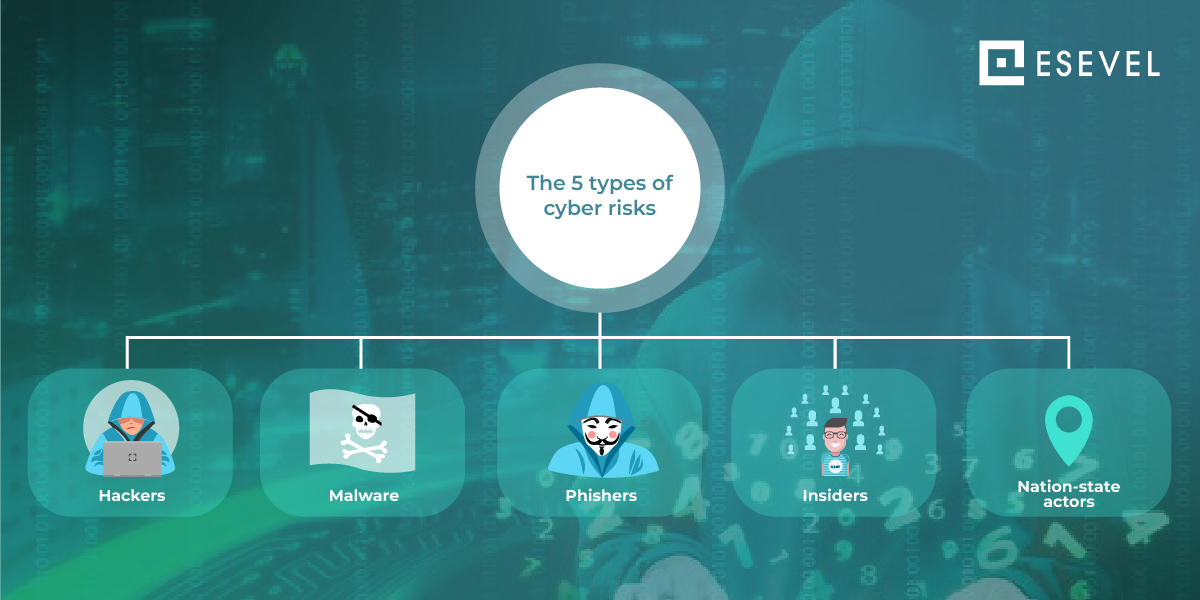 esevel.com
esevel.com
Determine Cyber Security Risks And Threats Cyber Risk Assessment PPT
 www.slideteam.net
www.slideteam.net
The Complete Guide To Cybersecurity Risks And Controls ( PDFDrive )-27
 www.studocu.com
www.studocu.com
1. Cybersecurity Risk Landscape
 paxdocs.com
paxdocs.com
The Complete Guide To Cybersecurity Risks And Controls ( PDFDrive )-69
 www.studocu.com
www.studocu.com
Risk Advisory | Cybersecurity Risks
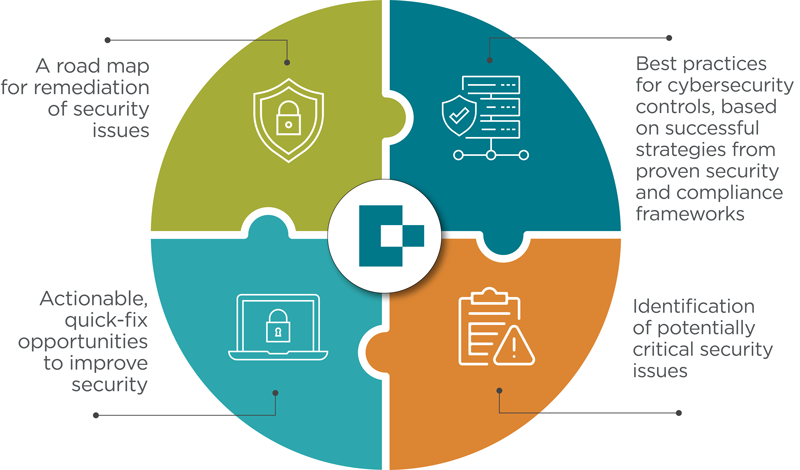 www.pbmares.com
www.pbmares.com
Essential Components Of Cyber Risk Prevention Strategy Information PDF
 www.slidegeeks.com
www.slidegeeks.com
Solved Which Of The Following Is A Reason To Use A | Chegg.com
 www.chegg.com
www.chegg.com
Solved Question 2.From The Following Choices, Select The | Chegg.com
 www.chegg.com
www.chegg.com
Understanding Cybersecurity Risks: Evolving Threats And Trends
 www.sprintzeal.com
www.sprintzeal.com
How Effectively Managing Risk Bolsters Cyber Protection - Flagship Networks
 www.flagshipnetworks.com
www.flagshipnetworks.com
(PDF) CYBERSECURITY CONSIDERATIONS & RISK … CONSIDERATIONS & RISK
 dokumen.tips
dokumen.tips
The Complete Guide To Cybersecurity Risks And Controls ( PDFDrive )-147
 www.studocu.com
www.studocu.com
Cybersecurity Risk Management 101 | PPT
 www.slideshare.net
www.slideshare.net
Cyber Risk Approaches For Security Protection Structure PDF
 www.slidegeeks.com
www.slidegeeks.com
Mitigating Cybersecurity Risks And Potential Threats | Peak Compliance
 www.pcacompliance.com
www.pcacompliance.com
Best Practices To Prevent Cyber Attacks Cyber Risk Assessment PPT Template
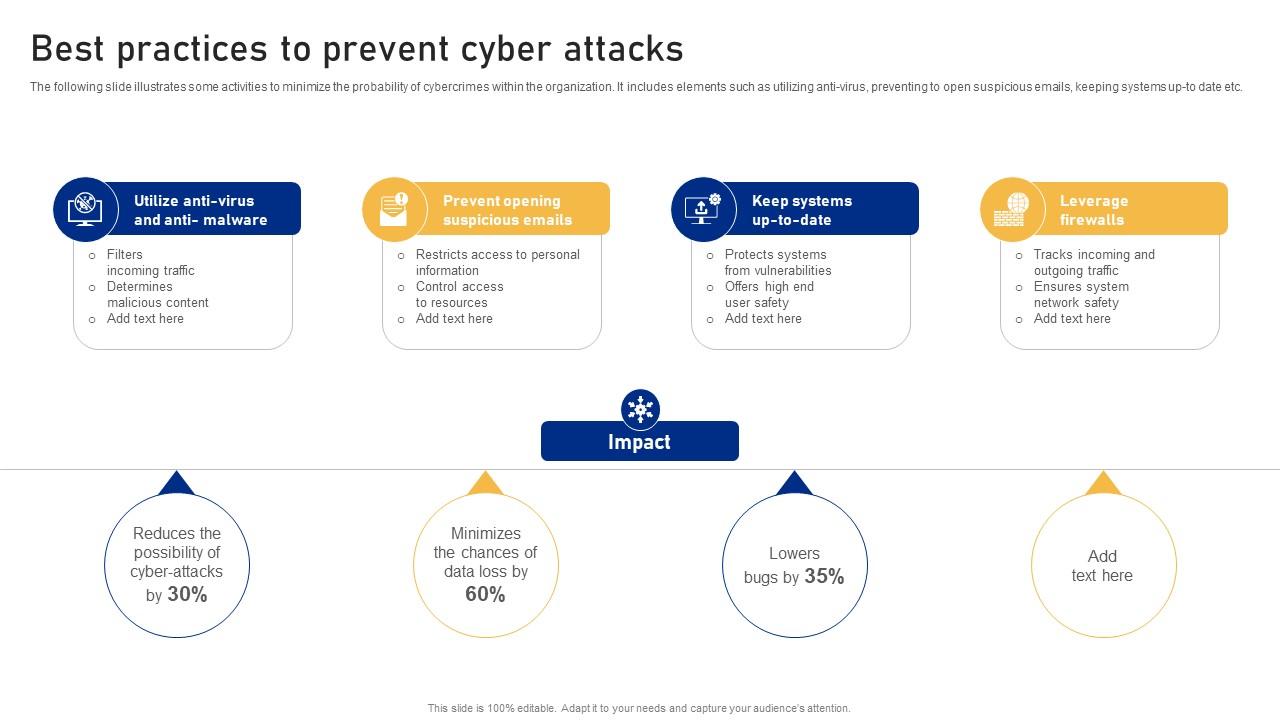 www.slideteam.net
www.slideteam.net
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
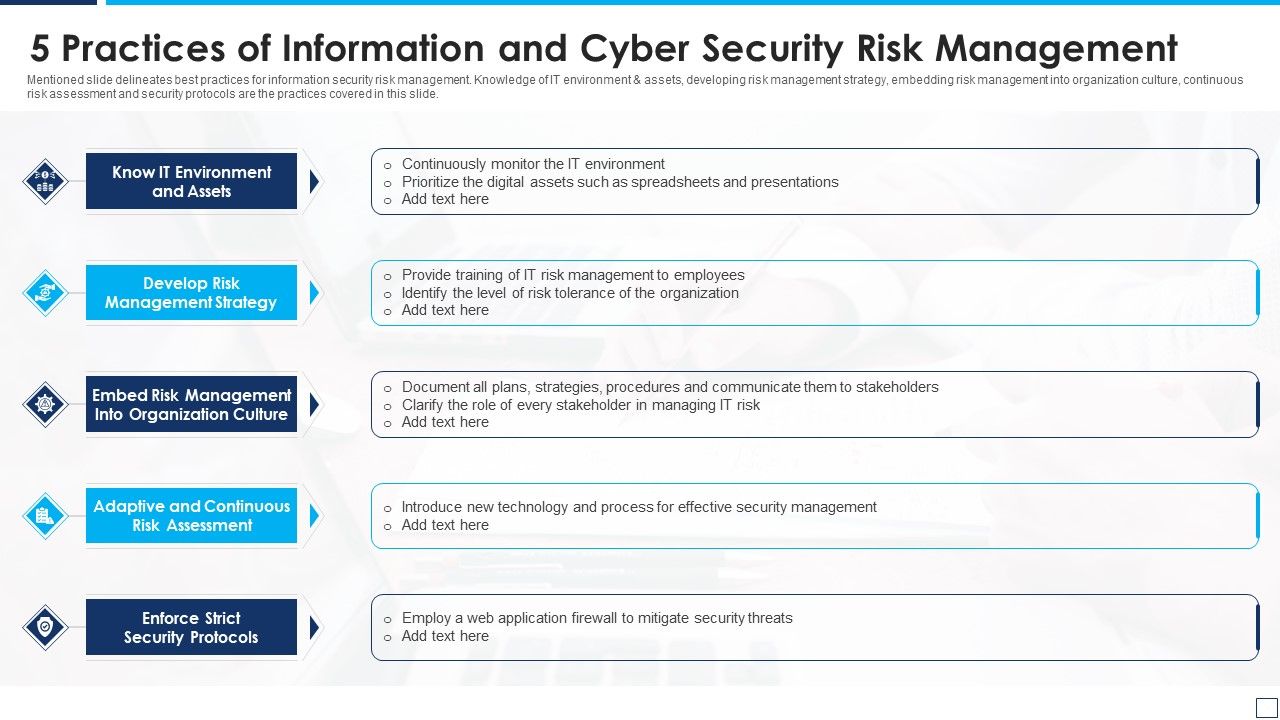 www.slidegeeks.com
www.slidegeeks.com
Mitigating Cybersecurity Risks And Potential Threats | Peak Compliance
 www.pcacompliance.com
www.pcacompliance.com
Cybersecurity Risk Assessment | FTG Australia
 ftg.com.au
ftg.com.au
The No-Nonsense 6-Step Cybersecurity Risk Assessment Checklist — Etactics
 etactics.com
etactics.com
The complete guide to cybersecurity risks and controls ( pdfdrive )-147. Determine cyber security risks and threats cyber risk assessment ppt. Mitigating cybersecurity risks and potential threats